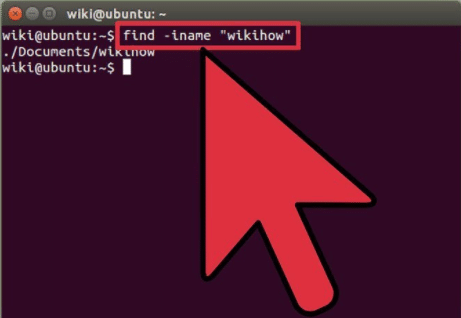
How To Install DenyHosts on CentOS 7
We explain all the steps you need to install DenyHosts in CentOS 7 and avoid attacks to the ssh
What is DenyHosts?
DenyHosts is a script that is used by many administrators and IT staff to avoid attacks on SSH servers, which can be known as dictionary-based or brute-force attacks because of the ability to decrypt the password.
As administrators, we can visualize in the CentOS 7 route the access attempts that have occurred to the system, and although as a general rule these accesses were not satisfactory it is better to prevent this type of efforts since some of them can occur and have serious security flaws.
/var/log/secure
Install DenyHosts in CentOS 7
First of all, we recommend updating the system using the command:
sudo yum update
Once the system is upgraded, we proceed to download the DenyHosts elements from the official repositories using the following command:
sudo rpm -Uvh http://mirror.metrocast.net/fedora/epel/6/i386/epel-release-6-8.noarch.rpm
Next we will install the DenyHosts packages using the following command:
sudo yum install denyhosts
Configure Parameters DenyHosts
Access the following route:
sudo nano /etc/hosts.allow
There it is necessary that we enter the IP address of our team, in this case it is 192.168.0.33 at the end of the file using the SSHD parameter:
sshd 192.168.0.33
Save Changes: Ctrl + O
Exit the editor: Ctrl + X
Then we will access the following file for its edition:
sudo nano /etc/hosts.deny
There we must add the next line to the end of the file:
sshd: ALL **
Save the changes. Once applied these changes we will use the following command to restart the service:
/etc/init.d/denyhosts restart
Main Configuration DenyHosts
Finally we can access the next route to adjust all DenyHosts values:
sudo nano /etc/denyhosts.conf
We will see the following:
There we can configure values such as:
PURGE_DENY: It allows us to define the time in which the IP addresses that have been blocked will be deleted.
BLOCK_SERVICE: Using this option we can define what services will be blocked to those devices that try to access without authorization.
DENY_THRESHOLD_INVALID: Using this alternative we can define the number of failed attempts of an account that does not exist
DENY_THRESHOLD_VALID: It does the same job as DENY_THRESHOLD_INVALID = but only for root users.
ADMIN_EMAIL: Through this option, we can define an email to receive reports about failed connections.
In the same way we can configure the parameters according to our needs.